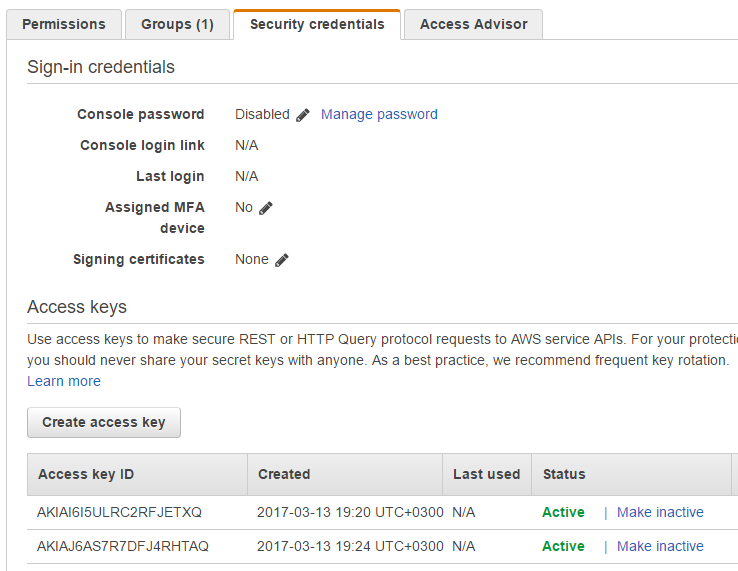
Server's Iam Secret Access Key From The Ec2 Metadata Endpoint . this endpoint can be used to retrieve data about the instance, some of which might be sensitive. # aws # ec2 # iam # security. An iam user is the starting point of the aws account. in such cases, we tend to encode the secret access key and access key id as part of the application for the. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. To solve the lab, exploit the xxe. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials. ec2 metadata server and iam role credentials.
from www.msp360.com
ec2 metadata server and iam role credentials. in such cases, we tend to encode the secret access key and access key id as part of the application for the. # aws # ec2 # iam # security. this endpoint can be used to retrieve data about the instance, some of which might be sensitive. An iam user is the starting point of the aws account. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. To solve the lab, exploit the xxe. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials.
How to Get AWS Access Key ID and Secret Access Key
Server's Iam Secret Access Key From The Ec2 Metadata Endpoint To solve the lab, exploit the xxe. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials. An iam user is the starting point of the aws account. in such cases, we tend to encode the secret access key and access key id as part of the application for the. # aws # ec2 # iam # security. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. To solve the lab, exploit the xxe. this endpoint can be used to retrieve data about the instance, some of which might be sensitive. ec2 metadata server and iam role credentials.
From www.radishlogic.com
How to create IAM User Access Keys using AWS Console Radish Logic Server's Iam Secret Access Key From The Ec2 Metadata Endpoint ec2 metadata server and iam role credentials. To solve the lab, exploit the xxe. # aws # ec2 # iam # security. An iam user is the starting point of the aws account. this endpoint can be used to retrieve data about the instance, some of which might be sensitive. each amazon ec2 instance contains metadata that. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From www.radishlogic.com
How to create IAM User Access Keys using AWS Console Radish Logic Server's Iam Secret Access Key From The Ec2 Metadata Endpoint imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials. # aws # ec2 # iam # security. To solve the lab, exploit the xxe. . Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From velog.io
AWS account security 관리 IAM Server's Iam Secret Access Key From The Ec2 Metadata Endpoint # aws # ec2 # iam # security. An iam user is the starting point of the aws account. this endpoint can be used to retrieve data about the instance, some of which might be sensitive. in such cases, we tend to encode the secret access key and access key id as part of the application for the.. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From www.msp360.com
How to Get AWS Access Key ID and Secret Access Key Server's Iam Secret Access Key From The Ec2 Metadata Endpoint ec2 metadata server and iam role credentials. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials. # aws # ec2 # iam # security.. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From docs.aws.amazon.com
Automatically rotate IAM user access keys at scale with AWS Server's Iam Secret Access Key From The Ec2 Metadata Endpoint # aws # ec2 # iam # security. this endpoint can be used to retrieve data about the instance, some of which might be sensitive. An iam user is the starting point of the aws account. ec2 metadata server and iam role credentials. To solve the lab, exploit the xxe. imdsv2 returns a secret token to the. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From infisical.com
AWS IAM User Infisical Server's Iam Secret Access Key From The Ec2 Metadata Endpoint # aws # ec2 # iam # security. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials. To solve the lab, exploit the xxe. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. . Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From www.youtube.com
how to get access key and secret key for IAM role in aws Project Server's Iam Secret Access Key From The Ec2 Metadata Endpoint To solve the lab, exploit the xxe. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. in such cases, we tend to encode the secret access key and access key id as part of the application for the. each amazon. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From rtfm.co.ua
AWS IAM users keys rotation, EC2 IAM Roles and Jenkins Server's Iam Secret Access Key From The Ec2 Metadata Endpoint An iam user is the starting point of the aws account. To solve the lab, exploit the xxe. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. this endpoint can be used to retrieve data about the instance, some of which. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From medium.com
Create AWS IAM Secret and Access Key using terraform by Jitender Negi Server's Iam Secret Access Key From The Ec2 Metadata Endpoint ec2 metadata server and iam role credentials. this endpoint can be used to retrieve data about the instance, some of which might be sensitive. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials. # aws # ec2 # iam # security. To solve the lab, exploit the xxe. in. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From www.youtube.com
Get Access/Secret Key 🔑 from EC2 Instance Metadata Data Exfiltration Server's Iam Secret Access Key From The Ec2 Metadata Endpoint imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. this endpoint can be used to retrieve data about the instance, some of which might be sensitive. ec2 metadata server and iam role credentials. To solve the lab, exploit the xxe.. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From medium.com
Migrating from IAM Secret and Access Keys to OIDC for Secure AWS Server's Iam Secret Access Key From The Ec2 Metadata Endpoint # aws # ec2 # iam # security. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. An iam user is the starting point of the aws account. in such cases, we tend to encode the secret access key and access. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From aws.amazon.com
AWS Identity and Access Management (IAM) AWS Database Blog Server's Iam Secret Access Key From The Ec2 Metadata Endpoint An iam user is the starting point of the aws account. # aws # ec2 # iam # security. this endpoint can be used to retrieve data about the instance, some of which might be sensitive. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From s3browser.com
AWS IAM Credentials How to Create New Access Key and Secret Key. How Server's Iam Secret Access Key From The Ec2 Metadata Endpoint in such cases, we tend to encode the secret access key and access key id as part of the application for the. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. this endpoint can be used to retrieve data about. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From advancedweb.hu
How to securely generate and store IAM Secret Access Keys with Server's Iam Secret Access Key From The Ec2 Metadata Endpoint imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials. # aws # ec2 # iam # security. this endpoint can be used to retrieve. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From docs.opsramp.com
Access Keys with IAM User Method OpsRamp Documentation Server's Iam Secret Access Key From The Ec2 Metadata Endpoint To solve the lab, exploit the xxe. # aws # ec2 # iam # security. in such cases, we tend to encode the secret access key and access key id as part of the application for the. imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From play.whizlabs.com
Create a VPC and launch an EC2 to publish a page using AWS CLI commands Server's Iam Secret Access Key From The Ec2 Metadata Endpoint To solve the lab, exploit the xxe. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials. # aws # ec2 # iam # security. this endpoint can be used to retrieve data about the instance, some of which might be sensitive. imdsv2 returns a secret token to the software running. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From www.clouddefense.ai
How to get Admin Access to EC2 Instance by Attaching an IAM role/Policy Server's Iam Secret Access Key From The Ec2 Metadata Endpoint # aws # ec2 # iam # security. each amazon ec2 instance contains metadata that the aws cli can directly query for temporary credentials. in such cases, we tend to encode the secret access key and access key id as part of the application for the. this endpoint can be used to retrieve data about the instance,. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.
From www.msp360.com
How to Get AWS Access Key ID and Secret Access Key Server's Iam Secret Access Key From The Ec2 Metadata Endpoint imdsv2 returns a secret token to the software running on the ec2 instance, which will use the token as a password to make requests to imdsv2. An iam user is the starting point of the aws account. To solve the lab, exploit the xxe. # aws # ec2 # iam # security. this endpoint can be used to. Server's Iam Secret Access Key From The Ec2 Metadata Endpoint.